Deploy Tenant Restriction V2

Introduction
Microsoft Tenant Restriction v2 is a feature that allows you to limit what your users can access when they use an external account to sign in from your networks or devices. With the Tenant restrictions settings included with cross-tenant access settings, you can control the external apps that your Windows device users can access when they’re using external accounts. For example, let’s say a user in your organization has created a separate account in an unknown tenant, or an external organization has given your user an account that lets them sign in to their organization. You can use tenant restrictions to prevent the user from using some or all external apps while they’re signed in with the external account on your network or devices.
The Tenant restrictions V2 is now available as a public preview and it offers more features than its predecessor. It allows an organization admin to control whether your users can access external applications from your network or devices using externally issued identities, including accounts issued by external organizations and accounts created in unknown tenants.
How to deploy with Intune?
Sadly there is no default Intune Policy for this, so we need to create a workaround with the Microsoft provided admx files.
Step 1: Download the admx files
Go to the Microsoft Download Center and download the admx Template for Windows 10 November 2021 Update v2.0
Step 2: Upload the admx files to Intune
Go to the Intune Portal -> Devices -> Configuration Profiles -> Import ADMX -> select the downloaded admx file -> Upload

Step 3: Create a new Configuration Profile
- Go to the Intune Portal
- Devices
- Configuration Profiles
- Create Profile -> Windows 10 and later
- Setting Catalog -> search for “Tenant Restriction” -> select Cloud Policy Details
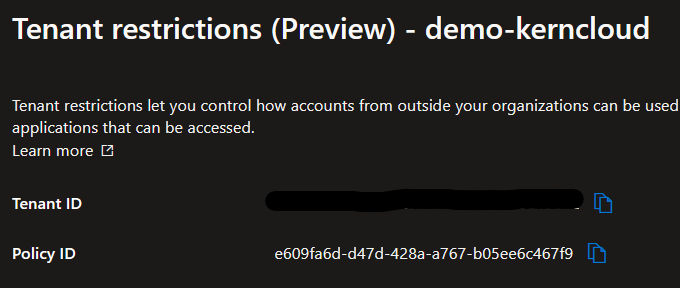
- Azure AD Directory ID
- Enable Firewall protection of Microsoft Endpoint
- Policy GUID
- Next
- Enabled “Cloud Policy Details”
- Enter Informations for:
- Azure AD Directory ID
- Enable Firewall protection of Microsoft Endpoint
- Policy GUID
! Informations got from the Cross-tenant access settings
- Next
- Scope Tags -> Next
- Assignments -> Next
- Review + Create -> Create

Result
Really easy, if you try to login with an Account from another Tenant you will get the following error message:

